NETSCALER ADM SECURITY ADVISORY

A safe, secure, and resilient infrastructure is the lifeline of any organization. NetScaler ADM security advisory highlights:
- Common Vulnerabilities and Exposures (CVEs) detection and remediation - Enables the identification of the CVEs putting the NetScaler instances at risk and recommends remediation.
- File Integrity Monitoring - Enables you to identify if any changes or additions have been made to your NetScaler build files.
As an administrator, which must ensure:
- Track any new Common Vulnerabilities and Exposures (CVEs), assess the impact of CVEs, understand the remediation, and resolve the vulnerabilities.
- Examine the integrity of your NetScaler build files.
Security advisory features
The following security advisory features help to protect the overall infrastructure.
CVEs:
| Features | Description |
|---|---|
| System scan | Scans all managed instances by default once a week. NetScaler ADM decides the date and time of system scans, and cannot be changed. |
| On-demand scan | Manually scan the instances when required. If the time elapsed after the last system scan is significant, the scan can run an on-demand scan to assess the current security posture. Or scan after a remediation has been applied, to assess the revised posture. |
| CVE impact analysis | Shows the results of all CVEs impacting the infrastructure and all the NetScaler instances getting impacted and suggests remediation. Use this information to apply remediation to fix security risks. |
| CVE reports | Stores copies of the last five scans, which the reports can be downloaded in CSV format and analyze them. |
| CVE repository | Gives a detailed view of all the NetScaler related CVEs that Citrix has announced since Dec 2019, that might impact the NetScaler infrastructure. These can be used this view to understand the CVEs in the security advisory scope and to learn more about the CVE. For information on CVEs that are not supported, see Unsupported CVEs in Security Advisory. |
File Integrity Monitoring:
| Features | Description |
|---|---|
| On-demand scan | Run an on-demand scan to get results on any file changes detected in NetScaler build files. |
| File integrity monitoring scan | Compares the binary hash value of the current NetScaler build files against the original binary hash and highlights if there are any file alterations or file additions. View the scan results under the File Integrity Monitoring tab. |
Points to note
- Security Advisory does not support NetScaler builds that have reached End of Life (EOL). NetScaler recommends upgrading to the NetScaler supported builds or versions.
- Instances supported for CVE detection: all NetScaler (SDX, MPX, VPX) and Gateway.
- Instances supported for File Integrity Monitoring: MPX, VPX instances, and Gateway.
- CVEs supported: All CVEs after Dec 2019.
NOTE:The detection and remediation of vulnerabilities impacting the NetScaler Gateway plug-in for Windows is not supported by the NetScaler ADM Security Advisory. For information on CVEs that are not supported, see Unsupported CVEs in Security Advisory.
- NetScaler ADM security advisory doesn’t account for any kind of feature misconfiguration while identifying the vulnerability.
- NetScaler ADM security advisory only supports the identification and remediation of the CVEs. It does not support identification and remediation of the security concerns that are highlighted in the Security article.
- Scope of NetScaler, Gateway releases: The feature is limited to main builds. Security advisory does not include any special build in its scope.
- Security advisory is not supported in Admin partition.
The following types of scan are available for CVEs:
- Version scan: This scan needs NetScaler ADM to compare the version of an NetScaler instance with the versions and builds on which the fix is available. This version comparison helps NetScaler ADM security advisory identify whether the NetScaler is vulnerable to the CVE. For example, if a CVE is fixed on an NetScaler release and build xx.yy, security advisory considers all the NetScaler instances on builds lesser than xx.yy as vulnerable. Version scan is supported today in security advisory.
- Config scan: This scan needs NetScaler ADM to match a pattern specific to the CVE scan with NetScaler config file (nsconf). If the specific config pattern is present in the NetScaler ns.conf file, the instance is considered vulnerable for that CVE. This scan is typically used with version scan. Config scan is supported today in security advisory.
- Custom scan: This scan needs NetScaler ADM to connect with the managed NetScaler instance, push a script to it, and run the script. The script output helps NetScaler ADM identify whether the NetScaler is vulnerable to the CVE. Examples include specific shell command output, specific CLI command output, certain logs, and existence or content of certain directories or files. Security Advisory also uses custom scans for multiple config patterns matches, if config scan cannot help with the same. For CVEs that require custom scans, the script runs every time your scheduled or on-demand scan runs. Learn more about the data collected and options for specific custom scans in the Security Advisory documentation for that CVE.
- The following scan is available for File Integrity Monitoring:
- File Integrity Monitoring scan: This scan needs NetScaler ADM to connect with the managed NetScaler instance. NetScaler ADM does a comparison of the hash values by running a script in NetScaler and collecting the current binary hash values for the NetScaler build files. After the comparison, NetScaler ADM provides the result with total number of existing files modified and total number of newly added files. As an administrator, you can contact your organization digital forensics for further investigations on the scan results.The following files are scanned:
/netscaler/bin, /sbin, /usr/bin, /usr/sbin, /usr/local/bin, /usr/local/sbin/lib, /libexec, /usr/lib, /usr/libexec, /usr/local/lib, /usr/lib32, /compat/etc- The rest of
/usr /root, /home, /mnt
- File Integrity Monitoring scan: This scan needs NetScaler ADM to connect with the managed NetScaler instance. NetScaler ADM does a comparison of the hash values by running a script in NetScaler and collecting the current binary hash values for the NetScaler build files. After the comparison, NetScaler ADM provides the result with total number of existing files modified and total number of newly added files. As an administrator, you can contact your organization digital forensics for further investigations on the scan results.The following files are scanned:
- Scans do not impact production traffic on NetScaler and do not alter any NetScaler configuration on NetScaler.
- NetScaler ADM Security Advisory does not support CVE mitigation. If you have applied mitigation (temporary workaround) to the NetScaler instance, ADM will still identify the NetScaler as a vulnerable NetScaler until you have completed remediation.
- For the FIPS instances, the CVE scan is not supported, but the File Integrity Monitoring scan is supported.
- Some file changes might occur as part of the normal operation of the device, while others might warrant further investigation. When reviewing file changes, the following might be helpful:
- Changes in the
/netscalerdirectory (in .html and .js files) might occur from the use of scripts or plug-ins. - The
/etcdirectory includes configuration files that might get changed by unexpected intervention after booting the system. - It would be unusual if there are:
- Reports in the
/bin,/sbin, or/libdirectories - New .php files in the
/netscalerdirectory
- Reports in the
- Changes in the
How to use the security advisory dashboard
To access the Security Advisory dashboard, from the NetScaler ADM GUI, navigate to Infrastructure > Instance Advisory > Security Advisory.The dashboard includes four tabs:
- Current CVEs
- File Integrity Monitoring
- Scan Log
- CVE Repository

IMPORTANT: In the Security Advisory GUI or report, all CVEs might not appear, and you might only see one CVE. As a workaround, click Scan Now > Scan CVEs to run an on-demand scan. After the scan is complete, all the CVEs in scope (approximately 15) appear in the UI or report.
On the upper-right corner of the dashboard is the settings icon, which allows you to:
- Enable and disable notifications (applicable only for CVE detection).You can receive the following notifications for CVEs impact.
- Email, Slack, PagerDuty, and ServiceNow notifications for CVE scan result changes and new CVEs that are added in CVE repository.
- Cloud notification for CVE impact scan result changes.
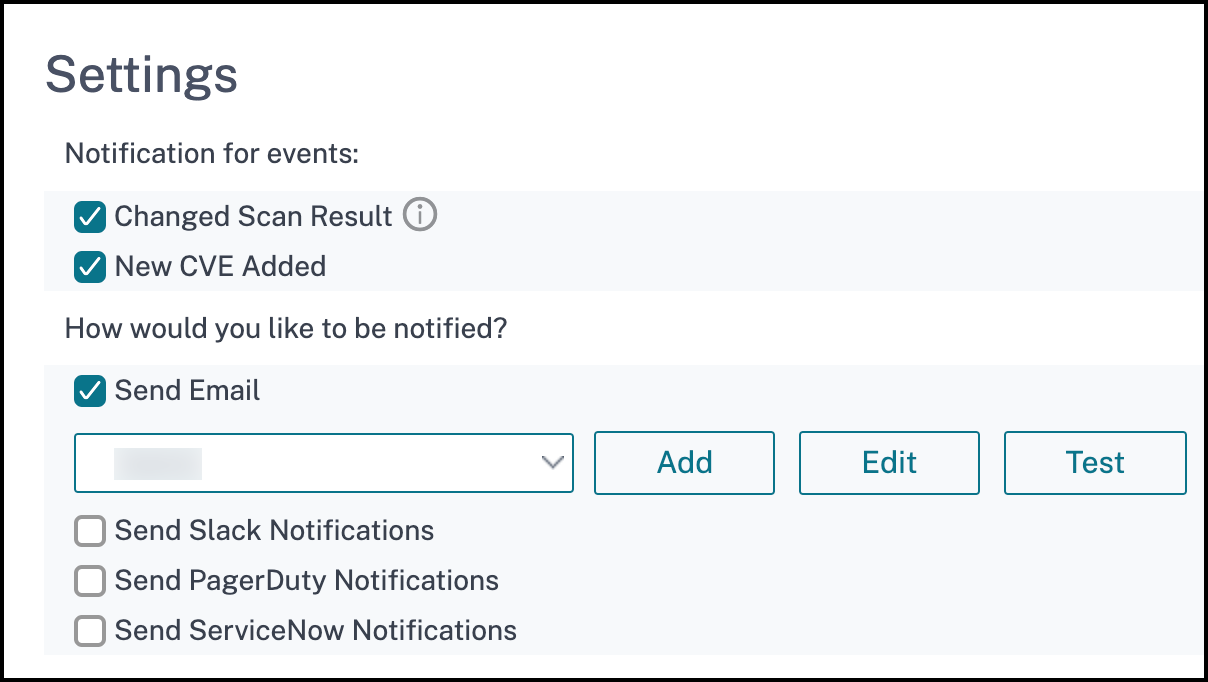
- Configure Custom Scan Settings (applicable only for CVEs)You can click the Custom Scan Settings list to view the additional settings checkbox. You have the option of selecting the checkbox and opt out of these CVE Custom scans. The impact of the CVEs that need a custom scan will not be evaluated for your NetScaler instances in the Security Advisory.

Current CVEs
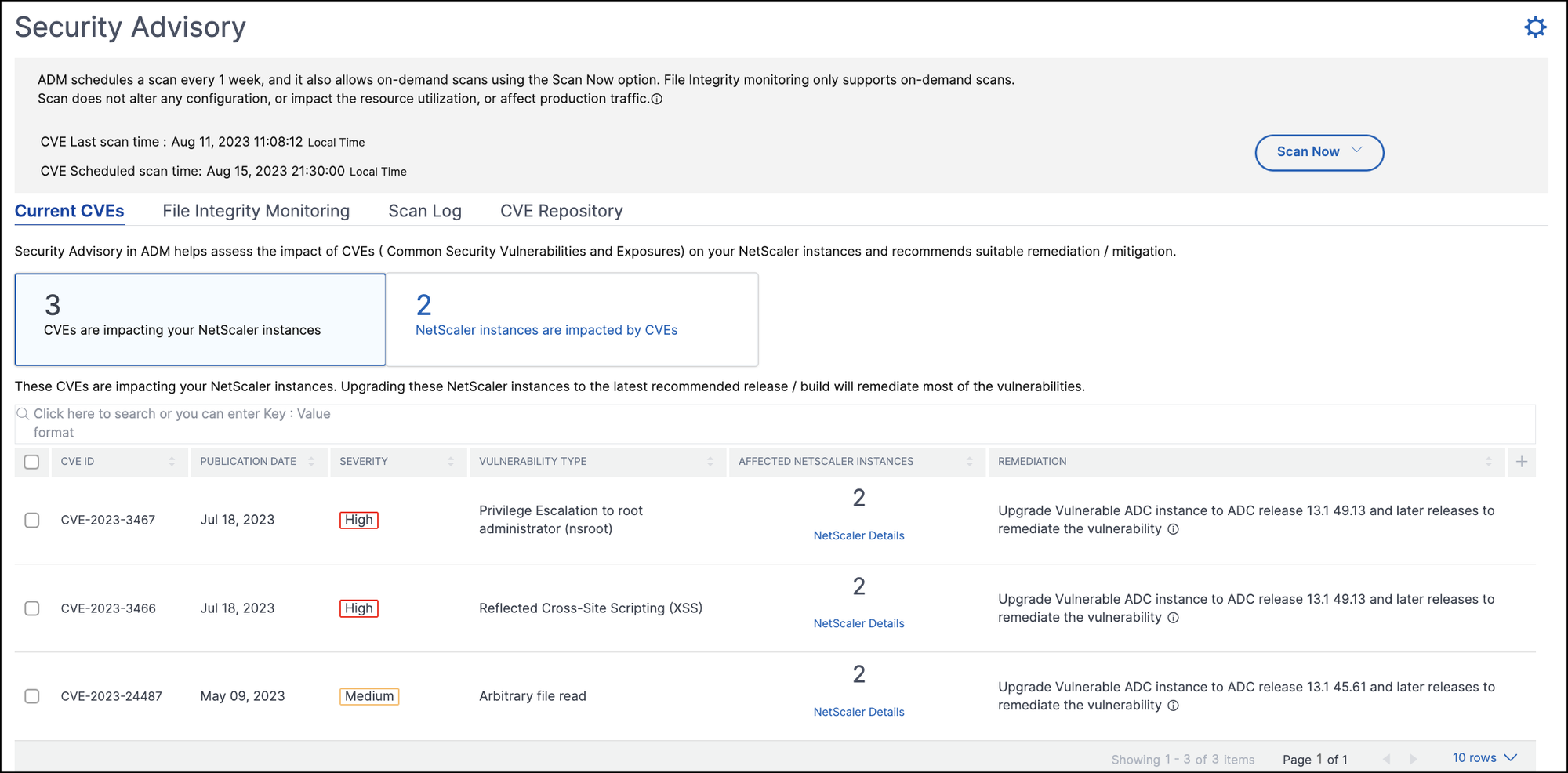
This tab shows the number of CVEs impacting your instances and also the instances that are impacted by CVEs. The tabs are not sequential, and as an admin, you can switch between these tabs depending on your use case. The table showing the number of CVEs impacting the NetScaler instances has the following details.
CVE ID: The ID of the CVE impacting the instances.
Publication date: The date the security bulletin was released for that CVE.
Severity score: The severity type (high/medium/critical) and score. To see the score, hover over the severity type.
Vulnerability type: The type of vulnerability for this CVE.
Affected NetScaler instances: The instance count that the CVE ID is impacting. On hover over, the list of NetScaler instances appears.
Remediation: The available remediations, which are upgrading the instance (usually) or applying configuration packs.The same instance can be impacted by multiple CVEs. This table helps you see how many instances one particular CVE or multiple selected CVEs are impacting. To check the IP address of the impacted instance, hover over NetScaler Details under:
Affected NetScaler Instances. To check the details of the impacted instance.
View Affected Instances at the bottom of the table. You can also add or remove columns in the table by clicking the plus sign. In this screen the number of CVEs impacting your instances is 3 CVEs and the instances that are impacted by these CVEs is two.
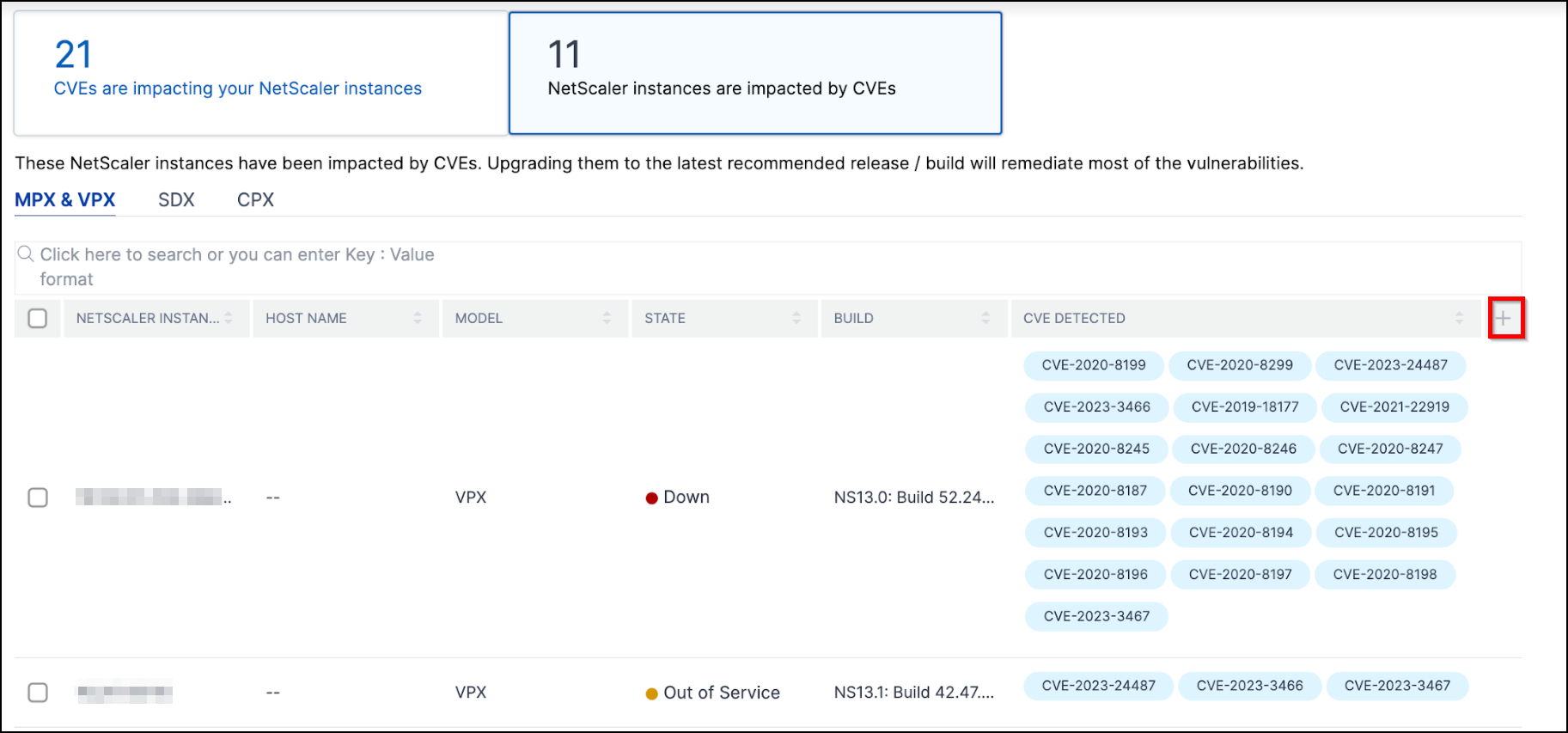
NetScaler instances are impacted by CVEs tab shows you all the affected NetScaler ADM NetScaler instances. The table shows the following details:
- NetScaler IP address
- Host name
- NetScaler model number
- State of the NetScaler
- Software version and build
- List of CVEs impacting the NetScaler.
Add or remove any of these columns according to the requirements needed, by clicking the + sign.
To fix the vulnerability issue, select the NetScaler instance and apply the recommended remediation. Most of the CVEs need upgrade as a remediation, while others need upgrade and an additional step as remediation.
- For CVE-2020-8300 remediation, see Remediate vulnerabilities for CVE-2020-8300.
- For CVE-2021-22927 and CVE-2021-22920, see Remediate vulnerabilities for CVE-2021-22927 and CVE-2021-22920.
- For CVE CVE-2021-22956, see Identify and remediate vulnerabilities for CVE-2021-22956
- For CVE CVE-2022-27509, see Remediate vulnerabilities for CVE-2022-27509
NOTE: If the NetScaler instances have customizations, see Upgrade considerations for customized NetScaler configurations before planning NetScaler upgrade.
Upgrade: To upgrade the vulnerable NetScaler instances to a release and build that has the fix. This detail can be seen in the remediation column.
To upgrade, select the instance and then click Proceed to upgrade workflow. In the upgrade workflow, the vulnerable NetScaler is auto-populated as the target NetScaler.
NOTEThe releases 12.0, 11,0, 10.5 and lower are already end of life (EOL). If your NetScaler instances are running on any of these releases, upgrade to a supported release.

The upgrade workflow starts. For more information on how to use NetScaler ADM to upgrade NetScaler instances, see Use jobs to upgrade NetScaler instances.
NOTE: The release and build to which is require, can be upgraded as when needed.
Please see:
See the advice under the remediation column to know which release and builds have the security fix. And accordingly select a supported release and build, which has not reached end of life yet.
File Integrity Monitoring
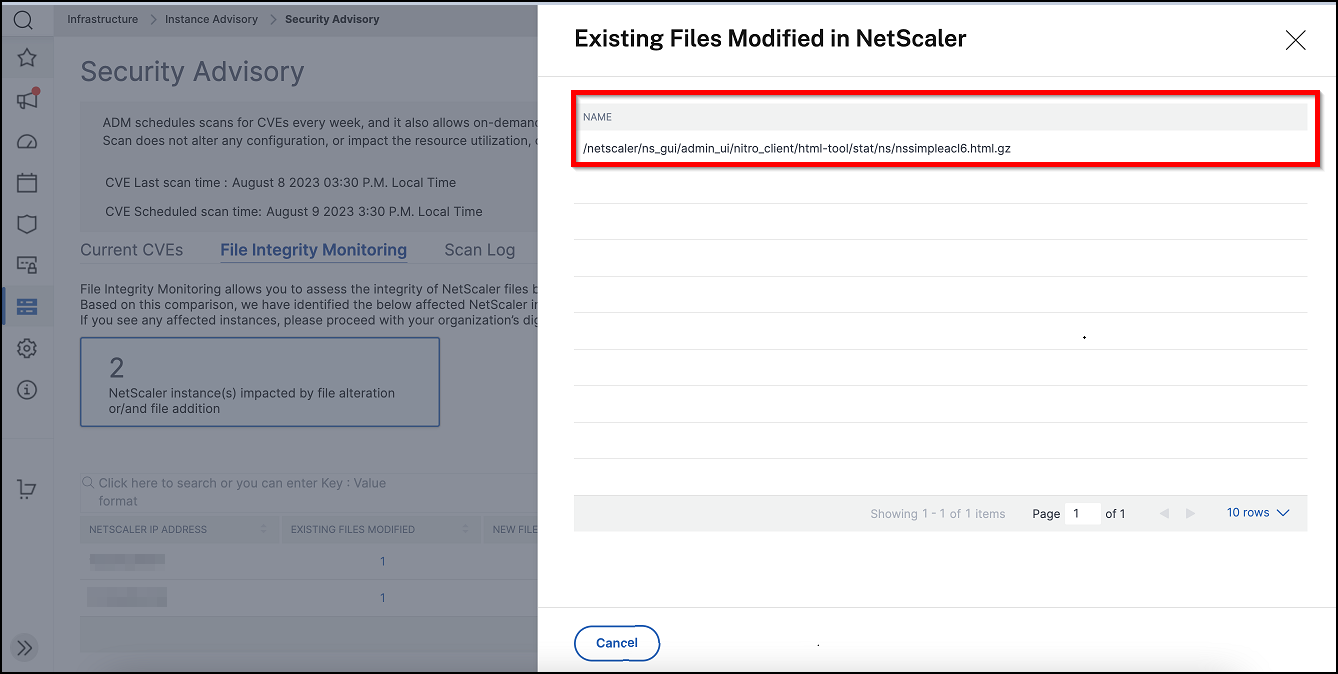
This tab shows the File Integrity Monitoring scan result with NetScaler instances that have any alterations or additions to the original NetScaler build files. The following example shows the scan result for two impacted NetScaler instances with existing files modified and new files added to the original build files.
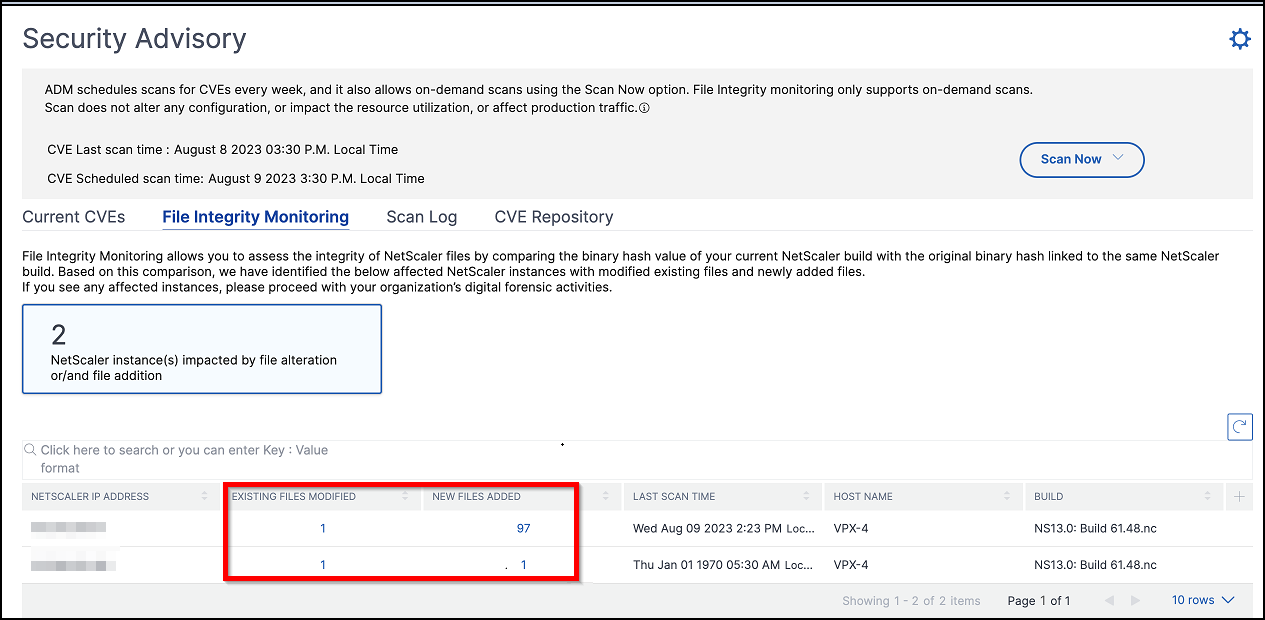
Click the numbers under Existing files modified and New files added to view details.
Scan Log (applicable only for CVEs)
The tab shows reports of the last five CVE scans, which include both default system scans and on-demand user-initiated scans. The report of each scan can be downloaded in CSV format. If an on-demand scan is in progress, look for completion status here. If any scan has failed, the status indicates that.

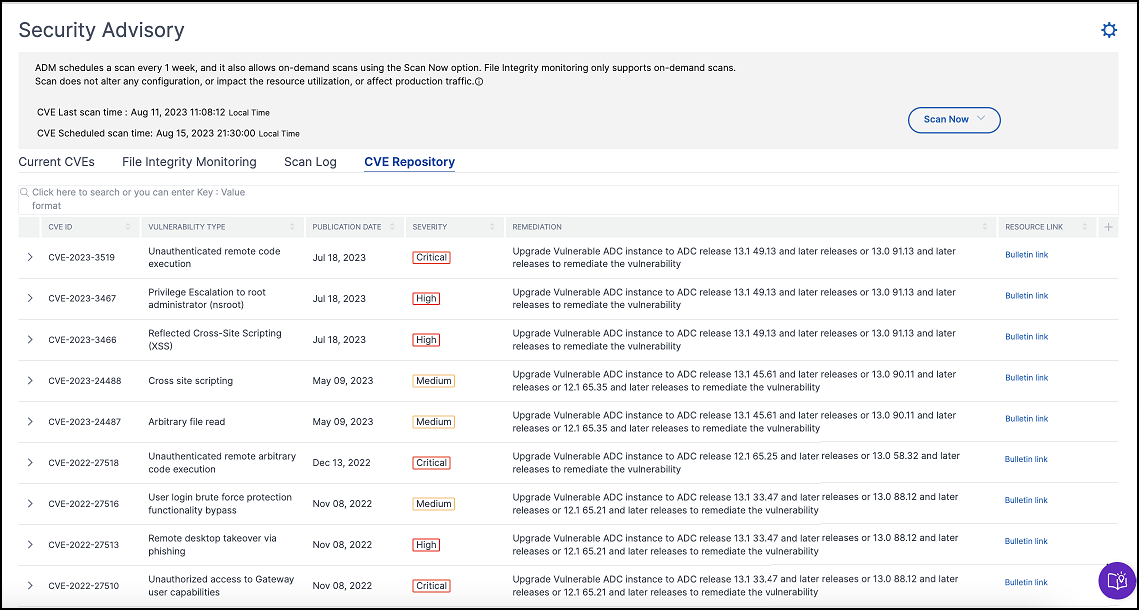
CVE Repository
This tab includes the latest information of all CVEs from December 2019, along with the following details:
- CVE IDs
- Vulnerability type
- Publication date
- Severity level
- Remediation
- Links to security bulletins
Scan Now
Scan the instances anytime, as and when required. Click Scan Now and select Scan CVEs, Scan Files, or Scan Both to get the latest security instances report.
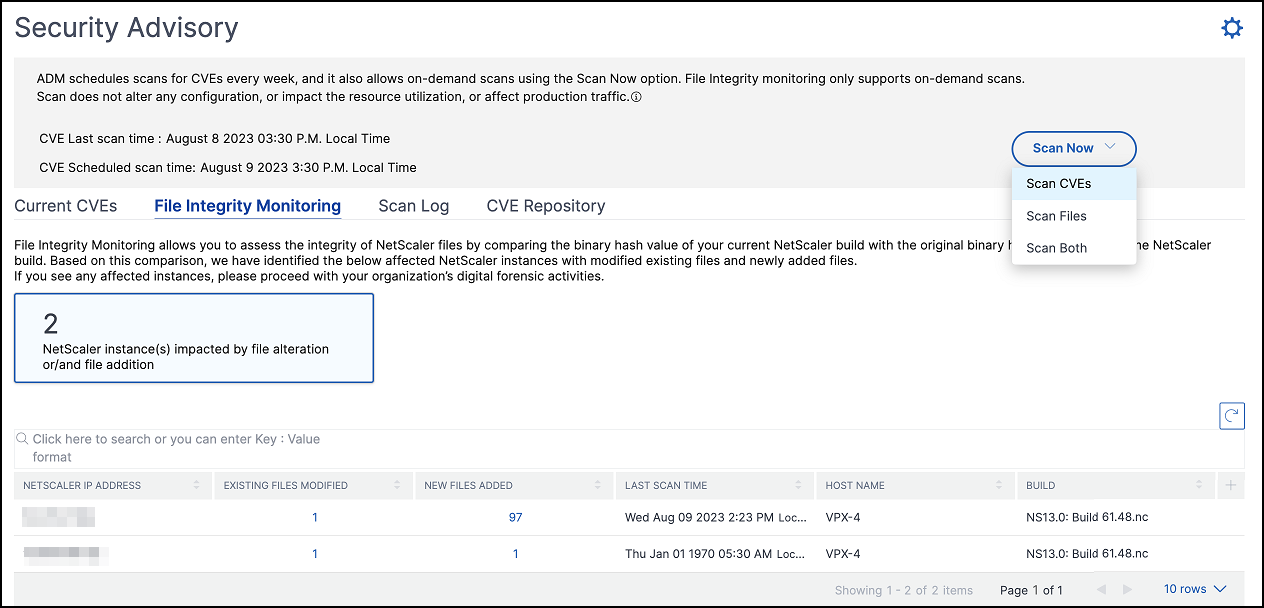
- Scan CVEs - Scans only for the CVEs that are impacting the NetScaler instances. Once the scanning is complete, the revised security details appear in the security advisory GUI. The report can be found under Scan Log, which is downloadable.

- Scan Files - Scans only for the file integrity monitoring and provides the result in the File Integrity Monitoring tab.
- Scan Both - Scans for both CVE detection and file integrity monitoring
NetScaler ADM takes a few minutes to complete the scan.
NOTES: Log shows the logs of only the last five CVE scans, which can be both scheduled or on demand.
Notification (applicable only for CVEs)
As an admin, receive Citrix Cloud notifications, which tell how many NetScaler instances are vulnerable with CVEs. To see the notifications, click the bell icon on the upper-right corner of the NetScaler ADM GUI.
DISCLAIMER: Please note that NetScaler File Integrity Monitoring (“the Feature”) is not capable of detecting all techniques, tactics, or procedures (TTPs) threat actors may use when targeting relevant environments. Threat actors change TTPs and infrastructure frequently, and therefore the Feature may be of limited to no forensic value as to certain threats. You are strongly advised to retain the services of experienced forensic investigators to assess your environment in connection with any possible threat. This document and the information contained in it is provided as-is. Cloud Software Group, Inc. makes no warranties or representations, whether express or implied, regarding the document or its contents, including, without limitation, that this document or the information contained in it, is error-free or meets any conditions of merchantability or fitness for a particular purpose.