SECURITY BEST PRACTICES FOR A .ICA FILE

Overview
Citrix Independent Computing Architecture (ICA) information is crucial for your Citrix deployment, enabling secure connections to applications and desktops for both internal and external users. This information is typically found in a .ICA file, which the Citrix Workspace app or browser uses to establish the connection. Given that ICA files provide access to your systems, implementing security best practices is essential. This paper will discuss various launch methods for ICA files, provide information recommendations, and outline best practices for securing this critical part of your infrastructure.
What is an ICA file?
When a user launches an application or desktop, StoreFront generates ICA information, which contains instructions for the client on how to connect to the VDA. This is a text document formatted like an INI file. It is referred to as an ICA 'file' whether it is stored on disk or held in memory. StoreFront creates this ICA file based on information from Citrix Virtual Apps and Desktops or Citrix Desktop as a Service (DaaS), along with its own configuration and logic.

Open an ICA file, name-value pairs will be shown, including the following:
| Field | Description |
| Address | For internal access, the IP address of the VDA to connect to. When a resource is accessed via a Gateway, this contains the Secure Ticket Authority (STA) ticket. |
| SSLProxyHost | If the resource is accessed via a Gateway, this contains the address of the Gateway. |
| LaunchReference | This contains the launch reference that is used to retrieve ancillary session data. This is a one-time ticket with a limited lifespan. |
| LogonTicket | This contains the logon ticket used to validate that the VDA is launching the connection that the DDC prepared. This is a one-time ticket with a limited lifespan. |
Note that the ICA file includes a field called ClearPassword. Despite its name, this is a legacy field that does not contain a password. Current versions of the Citrix Workspace app do not use this field.
Client access and launch methods
There are three ways for users to view their store and connect to their resources:
1. Citrix Workspace App: This method offers the best and most secure experience. It avoids using unmanaged web browsers, securely handles ICA files, and provides anti-keylogging protection during authentication.
2. Web Browser: Users can open their store and connect to resources within a web browser, which is useful when the Citrix Workspace app cannot be installed. ICA information is stored in memory within the browser.
3. Hybrid Launch: Users can open the store in their web browsers but launch resources in their locally installed Citrix Workspace app. This involves transferring ICA information between the browser and the locally installed app.
These mechanisms ensure flexibility and security in accessing resources. For more information on how your users can access their stores and launch resources, see StoreFront documentation.
Hybrid Launch mechanism details
This section describes how hybrid launches can transfer data between the browser and locally installed Citrix app.
Hybrid Launch using Citrix Workspace web extensions
Users can install Citrix Workspace web extensions on Chrome, Edge, and Safari. If the website detects this, it uses it to communicate securely with the locally installed Citrix Workspace app to launch applications. The user does not have the option to download ICA files to disk.
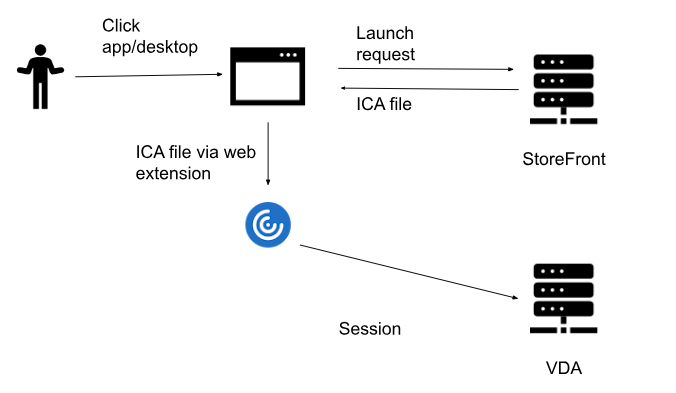
Hybrid Launch using Citrix Workspace launcher
Citrix Workspace app for Windows, Mac, and Linux includes a component called the Workspace app launcher. When the user launches a resource, the browser signals to the locally installed Citrix Workspace app to retrieve the ICA file from the StoreFront server.

Hybrid Launch using ICA download
If the browser cannot detect a locally installed Citrix Workspace via either Web Extensions or the Workspace launcher, it will download an ICA file when a user launches a resource. The user must then open this file with the Citrix Workspace app. 
Launch via Gateway
When launching a resource via a Gateway, StoreFront contacts a Secure Ticket Authority (STA) to obtain a ticket. For Citrix Virtual Apps and Desktops, this is typically the Delivery Controller, while for DaaS, it's usually the Cloud Connector, which proxies requests to the cloud ticketing authority. This ticket allows the user to connect to the resource for a limited time and is valid for a single use.
When the HDX client detects an SSLProxyHost in the ICA file, it contacts the Gateway with the STA ticket. The Gateway then verifies the ticket with the STA server and retrieves the address of the VDA to forward the traffic. Essentially, the Gateway acts as a reverse proxy between the HDX client and the VDA.
Recommendations
Absolutely, managing ICA files securely is crucial because they contain sensitive information that allows users to connect to Virtual Delivery Agents (VDAs). Implementing security best practices, such as using the Citrix Workspace app for handling ICA files, storing them in memory rather than on disk, and using code signing certificates, can significantly reduce the risk of unauthorized access.
Deploy the latest Citrix Workspace app
Using a locally installed Citrix Workspace app provides the most secure and seamless experience for launching VDAs, as the entire process is managed within the app. It is recommended deploying the Citrix Workspace app and configuring it to connect to the store whenever possible. Keeping the app updated ensures the benefits from the latest improvements and security enhancements.
Deploy Citrix Workspace Web Extensions
When native launch isn't feasible and hybrid launches are necessary, deploying Citrix Workspace web extensions is recommended. This ensures a reliable and secure hand-off between the browser and the locally installed Citrix Workspace app.
Disable ICA file downloads
In a hybrid launch scenario without Citrix Workspace Web Extensions or Citrix Workspace Launcher, the browser downloads an ICA file to disk. This file isn't launched immediately and requires the user to open it manually. This poses a security risk, as the file can be emailed to others or accessed by malicious software, potentially sending it to an attacker. To mitigate this risk, it's recommended to disable ICA file downloads for most deployments and use launch methods where the ICA file is transferred in-memory and launched immediately.
StoreFront 2402
StoreFront has introduced new settings to control ICA downloads. The first setting applies only to platforms where the Citrix Workspace launcher is supported (Windows, macOS, Linux). Typically, when users first open their store in a browser, they are prompted to open the Citrix Workspace launcher. Once they do this, the Citrix Workspace launcher is used for subsequent app launches. However, users can alternatively press 'Already installed,' which falls back to downloading ICA files. You can remove this option by clearing the "Show 'Already installed' link on the client detection page" setting.

The Citrix Workspace app for iOS and Android doesn't support the Workspace launcher, which means hybrid launches will always download ICA files. To prevent these downloads, you can select the option "Prevent ICA downloads on all platforms." Users will then need to add their store directly to the Citrix Workspace app for iOS and Android to enable native launches.

For more information, see StoreFront documentation
Earlier versions of StoreFront
To achieve the same results in earlier versions of StoreFront cab be done by applying the customization described in CTX584240, which involves preventing ICA downloads when initiating a hybrid launch.
Citrix Workspace
Citrix Workspace has a setting called “disallowIcaDownload” that hides the “Already installed” link on Windows and Mac, without affecting other operating systems. For other OS, it's recommended to open the store in a locally installed Citrix Workspace app. You can enforce protocol detection using the Workspace PowerShell module. However, this won't force users who previously clicked “Already installed” to use the Citrix Workspace launcher, so it's advisable to prompt users to clear their cookies after enabling this setting.
Reduce the lifetime of launch reference and logon tickets
Reducing session validity and launch times decreases an attacker's opportunity window if the system has been compromised.
The launch reference and logon tickets are valid for 200 seconds by default, but you can use the PowerShell `Set-
BrokerServiceConfigurationData` command to configure them with the `MaxSessionEstablishmentTimeSecs` setting.
For example: `Set-BrokerServiceConfigurationData Core.MaxSessionEstablishmentTimeSecs -SettingValue 100`
Ensure testing the configuration in the worst-case performance scenarios—if the ticket life is too low, it will expire before connecting to the VDA, and the launch will fail.
Prevent launching of unauthorized ICA files
There are concerns about the potential risks associated with malicious ICA files. These files can indeed be used by threat actors to exploit vulnerabilities, such as connecting to VDA-enabled local drive mappings and extracting data from the drives. This type of attack can be particularly dangerous if delivered through phishing emails, as unsuspecting users might open the file without realizing the threat it poses.
To mitigate these risks, it's crucial to implement security best practices, such as ensuring that ICA files are only opened from trusted sources, using up-to-date antivirus software, and educating users about the dangers of phishing emails. Additionally, employing multi-factor authentication and regularly updating software can help protect against such threats.
Prevent launching of ICA files from disk
To enhance security, it's recommended to configure Windows clients to refuse launching ICA files from disk if enabled in-memory ICA launches. This prevents users from launching ICA files received via email or other messaging systems. For detailed instructions, refer to the Citrix Workspace app for Windows documentation.
ICA Signing
ICA signing is a more comprehensive way to block users from opening ICA files from unauthorized sources in Windows. This involves configuring StoreFront to add a signature to the ICA file and configuring the Citrix Workspace app to only allow launches where that specific signature is present. Configure Workspace apps to either block unsigned launches completely or to prompt the user to allow unsigned launches.
Summary
There are numerous ways to enhance ICA security. While some methods may not be relevant to all organizations, it's crucial to adopt a layered and defense-in-depth strategy to implement as many as possible. Begin testing these recommendations today to strengthen your environment!
Resources
Product Documentation: StoreFront 2402 Long Term Service Release
OverviewProduct Documentation: Secure your StoreFront deployment
Product Documentation: Citrix WorkspaceTech Paper:
Security best practices for Citrix Virtual Apps and DesktopsTech Paper: