CREDENTIAL RISK - CITRIX HAS THE SOLUTION

Information courtesy of the Citrix Blog
In an age of constant digitization, where the lines between personal and professional spheres blend due to technological progress, security remains a pressing issue. Managing credentials across multiple apps and platforms presents a significant challenge, particularly with the common practice of reusing or slightly altering passwords.
The repercussions of credential exposure go beyond personal inconvenience, potentially jeopardizing corporate infrastructures.
This article explores how Citrix technology provides strong solutions to mitigate these risks and ensure a secure digital environment.
Understanding Account Take Over (ATO)
Account Takeover (ATO) happens when cybercriminals seize control of online accounts using stolen usernames and passwords. These credentials are often obtained from data breaches, social engineering, or phishing attacks and are traded in underground markets.
Cybercriminals use automated bots to exploit these credentials across various online services, from retail and finance to social media platforms, aiming to gain unauthorized access.
Common Methods of Credential Theft
Credential theft can be carried out through methods such as:
- Screen capture,
- Keyloggers, and
- Malware installation.
These tactics emphasize the critical need to implement strong security measures to protect sensitive information.
Mitigating ATO Risks with Citrix Technology
Citrix Enterprise Browser:
Grants secure, identity-aware access to browser-based applications without requiring a VPN.
- Imposes detailed controls for data loss prevention and threat mitigation, ensuring appropriate access.
- Adopts a zero-trust authentication approach, enabling secure access irrespective of user location, device, or risk profile.
- Includes contextual security policies such as anti-screen sharing, anti-keylogging, and data watermarking to prevent credential exposure.
- Empowers administrators to tailor security policies, manage browser settings, and oversee access to password managers and developer tools.
Citrix Secure Private Access (SPA).
- Provides Zero Trust Network Access (ZTNA) for all IT-approved applications, rebuilding trust with each interaction.
- Implements adaptive access and security controls to enforce contextual security, making it difficult for attackers to replicate user contexts.
- Offers browser isolation for secure web browsing, reducing the impact of potential breaches on corporate environments.
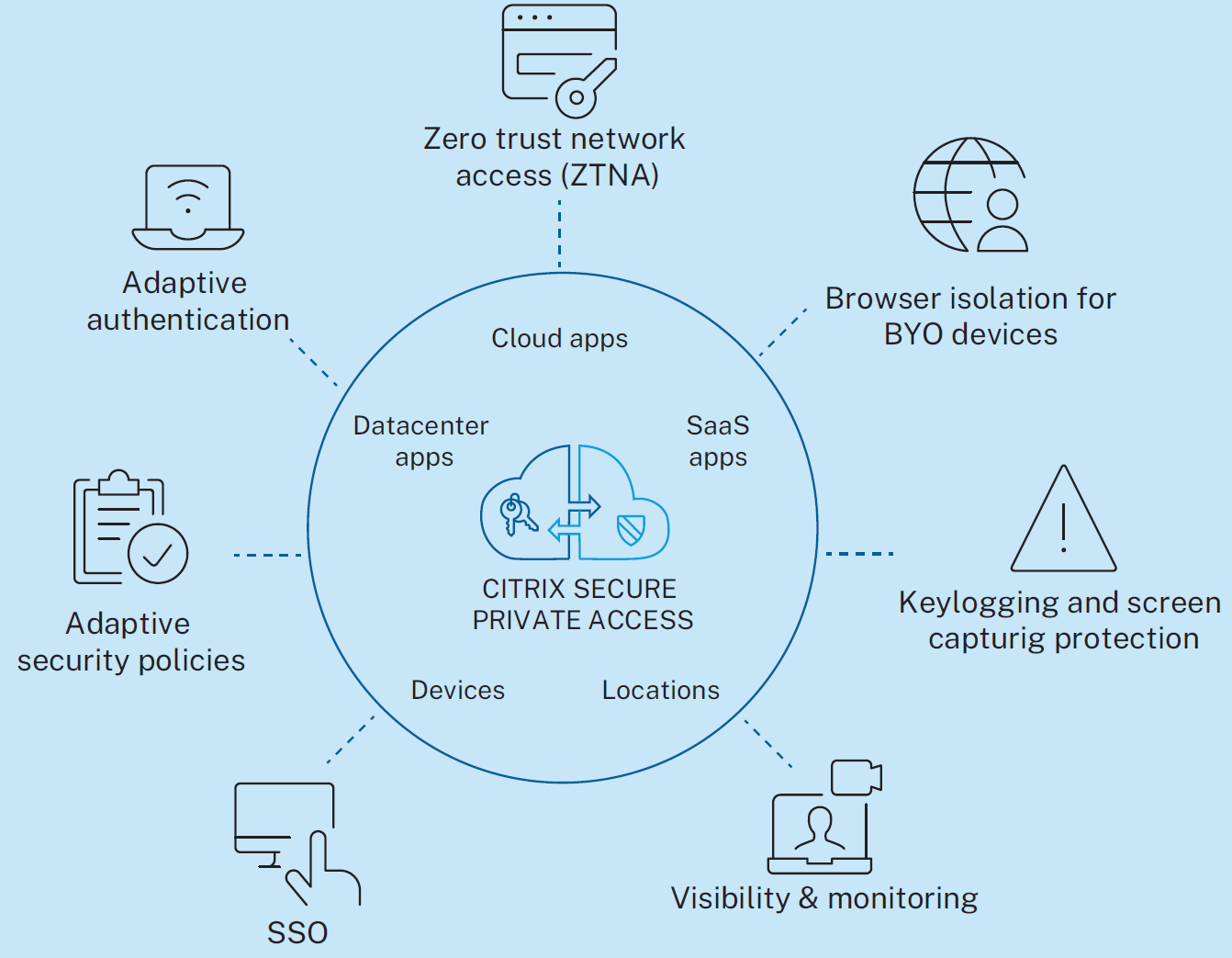
Figure 1 : Security features of Secure Private Access (SPA)
Conclusion: Enhancing Digital Security with Citrix Solutions
By utilizing Citrix Enterprise Browser and Citrix Secure Private Access, organizations can enable their employees to seamlessly access corporate networks and personal apps while reducing the risks of credential exposure and ATO.
These solutions not only ensure robust security but also enhance quality of life by offering freedom and flexibility in accessing digital resources.